 Drilling down a level deeper, this type of system provides different dynamic and risk-intelligent control based on attributes given to a specific user. Be familiar with this specific
device, as it may appear on the TICSA exam. The mandatory access control system provides the most restrictive protections, where the power to permit access falls entirely on system administrators. There are six access control models covered on the CISSP certification exam as well as different logical access control methods and several types of physical access controls. First, it gives the end-user complete control to set security level settings for other users which could result in users having higher privileges than theyre supposed to. Explanation: There are a number of access control models, some of them are as follows : Mandatory access control: Mandatory WebAccess control defined. These readings are compared to a database of authorized users to
determine identity. Companies should also consider using centralized authorization systems such as active directory. Biba is a setup where a user with lower clearance can read higher-level information (called read up) and a user with high-level clearance can write for lower levels of clearance (called write down). WebNIST SP 800-192 under Mandatory access control (MAC) A means of restricting access to system resources based on the sensitivity (as represented by a label) of the information contained in the system resource and the formal authorization (i.e., clearance) of users to access information of such sensitivity. ABAC allows you to use user attributes such as username, role, and security clearance. Once policies are set, they can use these attributes to read whether or not a user should have control. Role-based access control attributes permissions to a user based on their business responsibilities. WebHeathrow Terminal 5 is an airport terminal at Heathrow Airport, the main airport serving London.Opened in 2008, the main building in the complex is the largest free-standing structure in the United Kingdom. This would make it so that administrators could update records at night without interference from other users. Pearson may disclose personal information, as follows: This web site contains links to other sites. He holds a Master's degree in Information Assurance with GSEC and GCIH certifications. In short, stack RuBAC on top of RBAC to get the multi-level security your business needs. We may revise this Privacy Notice through an updated posting. SailPoints professional services team helps maximize your identity governance platform by offering assistance before, during, and after your implementation. Group policies are part of the Windows environment and allow for centralized management of access control to a network of computers utilizing the directory services of Microsoft called Active Directory. In their defense,
DAC grants administrative control of resources to the people responsible for
their everyday use. Accounting functions track usage of computing resources on a cost basis. In the world of information security, one would look at this as granting an individual permission to get onto a network via a username and password, allowing them access to files, computers or other hardware or software the person requires and ensuring they have the right level of permission (i.e., read-only) to do their job. While Pearson does not sell personal information, as defined in Nevada law, Nevada residents may email a request for no sale of their personal information to NevadaDesignatedRequest@pearson.com. Pearson uses this information for system administration and to identify problems, improve service, detect unauthorized access and fraudulent activity, prevent and respond to security incidents, appropriately scale computing resources and otherwise support and deliver this site and its services. Read our vulnerabilities article for more information on the latest cybersecurity risks here. Multilevel security is an IT security policy that enables businesses to use a hierarchical system of security. The SailPoint Advantage, We empower every SailPoint employee to feel confident in who they are and how they work, Led by the best in security and identity, we rise up, Living our values and giving our crew opportunities to think bigger and do better, every day, Check out our current SailPoint Crew openings, See why our crew voted us the best place to work, Read on for the latest press releases from SailPoint, See where SailPoint has been covered in the news, Reach out with any questions or to get more information. Attribute-based access control (ABAC) is another type of access control.
Drilling down a level deeper, this type of system provides different dynamic and risk-intelligent control based on attributes given to a specific user. Be familiar with this specific
device, as it may appear on the TICSA exam. The mandatory access control system provides the most restrictive protections, where the power to permit access falls entirely on system administrators. There are six access control models covered on the CISSP certification exam as well as different logical access control methods and several types of physical access controls. First, it gives the end-user complete control to set security level settings for other users which could result in users having higher privileges than theyre supposed to. Explanation: There are a number of access control models, some of them are as follows : Mandatory access control: Mandatory WebAccess control defined. These readings are compared to a database of authorized users to
determine identity. Companies should also consider using centralized authorization systems such as active directory. Biba is a setup where a user with lower clearance can read higher-level information (called read up) and a user with high-level clearance can write for lower levels of clearance (called write down). WebNIST SP 800-192 under Mandatory access control (MAC) A means of restricting access to system resources based on the sensitivity (as represented by a label) of the information contained in the system resource and the formal authorization (i.e., clearance) of users to access information of such sensitivity. ABAC allows you to use user attributes such as username, role, and security clearance. Once policies are set, they can use these attributes to read whether or not a user should have control. Role-based access control attributes permissions to a user based on their business responsibilities. WebHeathrow Terminal 5 is an airport terminal at Heathrow Airport, the main airport serving London.Opened in 2008, the main building in the complex is the largest free-standing structure in the United Kingdom. This would make it so that administrators could update records at night without interference from other users. Pearson may disclose personal information, as follows: This web site contains links to other sites. He holds a Master's degree in Information Assurance with GSEC and GCIH certifications. In short, stack RuBAC on top of RBAC to get the multi-level security your business needs. We may revise this Privacy Notice through an updated posting. SailPoints professional services team helps maximize your identity governance platform by offering assistance before, during, and after your implementation. Group policies are part of the Windows environment and allow for centralized management of access control to a network of computers utilizing the directory services of Microsoft called Active Directory. In their defense,
DAC grants administrative control of resources to the people responsible for
their everyday use. Accounting functions track usage of computing resources on a cost basis. In the world of information security, one would look at this as granting an individual permission to get onto a network via a username and password, allowing them access to files, computers or other hardware or software the person requires and ensuring they have the right level of permission (i.e., read-only) to do their job. While Pearson does not sell personal information, as defined in Nevada law, Nevada residents may email a request for no sale of their personal information to NevadaDesignatedRequest@pearson.com. Pearson uses this information for system administration and to identify problems, improve service, detect unauthorized access and fraudulent activity, prevent and respond to security incidents, appropriately scale computing resources and otherwise support and deliver this site and its services. Read our vulnerabilities article for more information on the latest cybersecurity risks here. Multilevel security is an IT security policy that enables businesses to use a hierarchical system of security. The SailPoint Advantage, We empower every SailPoint employee to feel confident in who they are and how they work, Led by the best in security and identity, we rise up, Living our values and giving our crew opportunities to think bigger and do better, every day, Check out our current SailPoint Crew openings, See why our crew voted us the best place to work, Read on for the latest press releases from SailPoint, See where SailPoint has been covered in the news, Reach out with any questions or to get more information. Attribute-based access control (ABAC) is another type of access control.  Access more information about IT Security here. Yet, this approach needs another level of maintenance and constant monitoring. The enterprise no longer has to tightly monitor the complicated web of policies and access control lists, because AI simplifies visibility at a high level. WebMission The Office of Foreign Assets Control ("OFAC") of the US Department of the Treasury administers and enforces economic and trade sanctions based on US foreign policy and national security goals against targeted foreign countries and regimes, terrorists, international narcotics traffickers, those engaged in activities related to the proliferation of HID is a world leader in access control, securing assets with a combination of physical security, and logical access control.
Access more information about IT Security here. Yet, this approach needs another level of maintenance and constant monitoring. The enterprise no longer has to tightly monitor the complicated web of policies and access control lists, because AI simplifies visibility at a high level. WebMission The Office of Foreign Assets Control ("OFAC") of the US Department of the Treasury administers and enforces economic and trade sanctions based on US foreign policy and national security goals against targeted foreign countries and regimes, terrorists, international narcotics traffickers, those engaged in activities related to the proliferation of HID is a world leader in access control, securing assets with a combination of physical security, and logical access control.  Discover how to better protect your business using advanced malware protection. yourfile.docx) is level 600 and the employee had a level of 500, the employee would not be able to access yourfile.docx due to the higher level (600) associated with the file. They can only access points that the system owners allow them to access. This is because it assigns permissions at the Kernel level. As painful as it may seem (and inconvenient at times), there are reasons why access control comes into play for a scenario like this. Process of verifying a user's identity
through the use of a shared secret (such as a password), a physical token (such
as a key), or a biometric measure (such as a fingerprint). Risk-Based Access Control is a dynamic access control model that determines access based on the level of evaluated risk involved in the transaction. How is access tracked? Secondly, the object access in DAC uses an access control list (ACL) authorization. As the most common access control system, it determines access based on the users role in the companyensuring lower-level employees arent gaining access to high-level information. For example, someone in human resources does not need access to private marketing materials, and marketing employees dont need access to employee salaries. In addition, it also provides you with better operational efficiency than MAC. All Rights Reserved. Since the OS controls the system it runs on, the kernel has complete control over everything. The big issue with this access control model is that if John requires access to other files, there has to be another way to do it since the roles are only associated with the position; otherwise, security managers from other organizations could get access to files they are unauthorized for. If a user no longer desires our service and desires to delete his or her account, please contact us at customer-service@informit.com and we will process the deletion of a user's account. RBAC makes life easier for the system administrator of the organization. Access control models bridge the gap in abstraction between policy and mechanism.
Discover how to better protect your business using advanced malware protection. yourfile.docx) is level 600 and the employee had a level of 500, the employee would not be able to access yourfile.docx due to the higher level (600) associated with the file. They can only access points that the system owners allow them to access. This is because it assigns permissions at the Kernel level. As painful as it may seem (and inconvenient at times), there are reasons why access control comes into play for a scenario like this. Process of verifying a user's identity
through the use of a shared secret (such as a password), a physical token (such
as a key), or a biometric measure (such as a fingerprint). Risk-Based Access Control is a dynamic access control model that determines access based on the level of evaluated risk involved in the transaction. How is access tracked? Secondly, the object access in DAC uses an access control list (ACL) authorization. As the most common access control system, it determines access based on the users role in the companyensuring lower-level employees arent gaining access to high-level information. For example, someone in human resources does not need access to private marketing materials, and marketing employees dont need access to employee salaries. In addition, it also provides you with better operational efficiency than MAC. All Rights Reserved. Since the OS controls the system it runs on, the kernel has complete control over everything. The big issue with this access control model is that if John requires access to other files, there has to be another way to do it since the roles are only associated with the position; otherwise, security managers from other organizations could get access to files they are unauthorized for. If a user no longer desires our service and desires to delete his or her account, please contact us at customer-service@informit.com and we will process the deletion of a user's account. RBAC makes life easier for the system administrator of the organization. Access control models bridge the gap in abstraction between policy and mechanism. 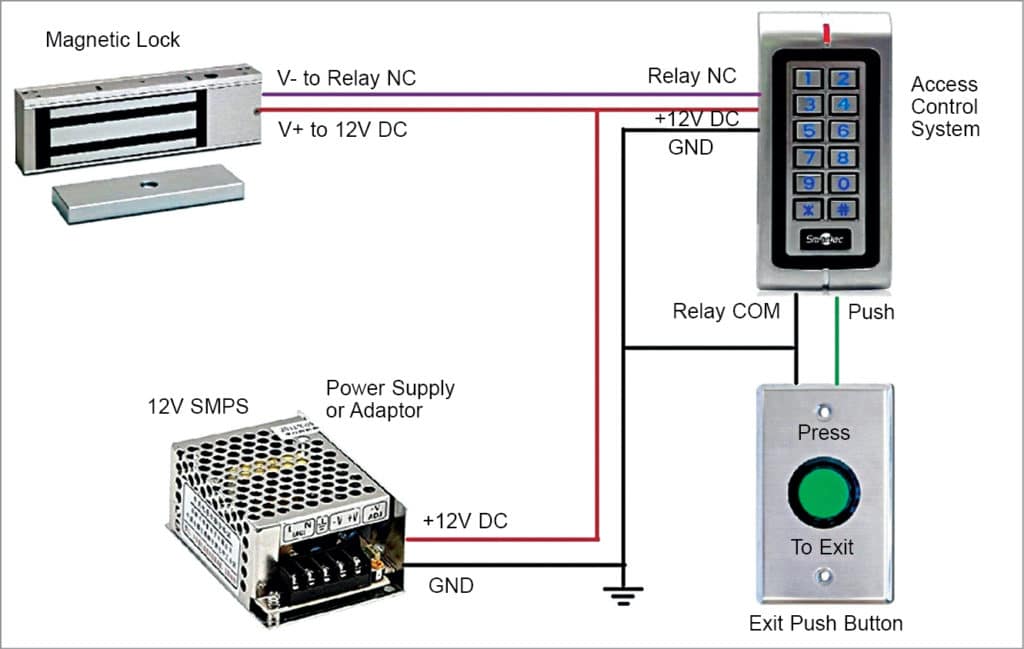 These systems require use of a special-
purpose hardware device that functions like a customized key to gain system
access. California residents should read our Supplemental privacy statement for California residents in conjunction with this Privacy Notice. Authentication Methods These three types of authentication are
commonly referred to as something you have (physical token), something you know
(shared secret), and something you are (biometric measure). Theoretically, these individuals would be best suited to
assess a user's "need to know." Because individual users and activities can be tracked as such, accounting
also provides IT staff and managers with a tool to look for possible abuse of
company resources. As access control moves into the future, the responsibility of managing the systems will continue to shift away from people and towards technology. Attribute-based access control (ABAC) is an approach to data security that permits or restricts data access based on assigned user, object, action and environmental attributes. WebAfter the authentication process has been completed, user authorization can be determined in one of several ways: Mandatory access control (MAC): Mandatory access control Unlike RBAC, for instance, which uses group-level permissions, DAC uses object-level permissions. This means that the operating system is going to provide the limits on how much access someone will have to a particular object. Such marketing is consistent with applicable law and Pearson's legal obligations. For example, who gets access to what? Video surveillance can also be utilized in mantraps. The "AAA" concept is the cornerstone of any systematic discipline
of security (IT or otherwise). A Answer: C The principle of least privilege ensures that users (subjects) are granted only the most restrictive rights they need to perform their work tasks and job functions. As you might have guessed, this system grants permissions based on structured rules and policies. The SailPoint Advantage. To assure the safety of an access control system, it is essential tomake certain that the access control configuration (e.g., access control model) will not result in the leakage of permissions to an unauthorized principle. The information age is starting to transform fishingworldwide, Top 10 mind-blowing facts about the internet, Treasury: Victims paid $590 million to ransomware hackers in first half of 2021. Paper access logs are common in many places for physical security. Access rights in this method are designed around a collection of variables that map back to the businesssuch as resources, needs, environment, job, location, and more. Policies define an object owner, and many owners can exist within the business. An. The Kiowa County Press is an independent newspaper published in Eads, Kiowa County, Colorado, and to the world at KiowaCountyPress.net. WebEnforce the least restrictive rights required by users to complete assigned tasks. WebGun laws and policies, collectively referred to as firearms regulation or gun control, regulate the manufacture, sale, transfer, possession, modification, and use of small arms by civilians. A trojan is a type of malware that downloads onto a computer disguised as a genuine piece of software. Access control is one of the easiest and most effective ways to meet your security needs. For example, we could deny access based on the environment (e.g., time of day) or action (e.g., deleting records). Websmall equipment auction; ABOUT US.
These systems require use of a special-
purpose hardware device that functions like a customized key to gain system
access. California residents should read our Supplemental privacy statement for California residents in conjunction with this Privacy Notice. Authentication Methods These three types of authentication are
commonly referred to as something you have (physical token), something you know
(shared secret), and something you are (biometric measure). Theoretically, these individuals would be best suited to
assess a user's "need to know." Because individual users and activities can be tracked as such, accounting
also provides IT staff and managers with a tool to look for possible abuse of
company resources. As access control moves into the future, the responsibility of managing the systems will continue to shift away from people and towards technology. Attribute-based access control (ABAC) is an approach to data security that permits or restricts data access based on assigned user, object, action and environmental attributes. WebAfter the authentication process has been completed, user authorization can be determined in one of several ways: Mandatory access control (MAC): Mandatory access control Unlike RBAC, for instance, which uses group-level permissions, DAC uses object-level permissions. This means that the operating system is going to provide the limits on how much access someone will have to a particular object. Such marketing is consistent with applicable law and Pearson's legal obligations. For example, who gets access to what? Video surveillance can also be utilized in mantraps. The "AAA" concept is the cornerstone of any systematic discipline
of security (IT or otherwise). A Answer: C The principle of least privilege ensures that users (subjects) are granted only the most restrictive rights they need to perform their work tasks and job functions. As you might have guessed, this system grants permissions based on structured rules and policies. The SailPoint Advantage. To assure the safety of an access control system, it is essential tomake certain that the access control configuration (e.g., access control model) will not result in the leakage of permissions to an unauthorized principle. The information age is starting to transform fishingworldwide, Top 10 mind-blowing facts about the internet, Treasury: Victims paid $590 million to ransomware hackers in first half of 2021. Paper access logs are common in many places for physical security. Access rights in this method are designed around a collection of variables that map back to the businesssuch as resources, needs, environment, job, location, and more. Policies define an object owner, and many owners can exist within the business. An. The Kiowa County Press is an independent newspaper published in Eads, Kiowa County, Colorado, and to the world at KiowaCountyPress.net. WebEnforce the least restrictive rights required by users to complete assigned tasks. WebGun laws and policies, collectively referred to as firearms regulation or gun control, regulate the manufacture, sale, transfer, possession, modification, and use of small arms by civilians. A trojan is a type of malware that downloads onto a computer disguised as a genuine piece of software. Access control is one of the easiest and most effective ways to meet your security needs. For example, we could deny access based on the environment (e.g., time of day) or action (e.g., deleting records). Websmall equipment auction; ABOUT US. 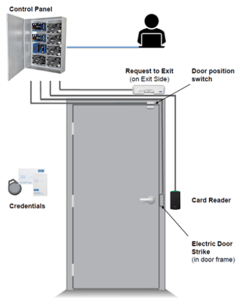 Choosing the Best Content Filtering Software for Your Small Business. In this article. Pearson may send or direct marketing communications to users, provided that. Keeping this in mind, experts agree that the longer the password is, the harder it is to crack, provided the user remembers it and uses many different characters and non-keyboard type characters in creating it. Where the MAC approach is rigid and low-effort, a DAC system is flexible and high-effort. Rule-Based Access Control will dynamically assign roles to users based on criteria defined by the custodian or system administrator. Sign up for the TechGenix newsletter and the latest tech and cybersecurity news right here. Mandatory access control is widely considered the most restrictive access control model in existence. Access control leverages security measures like authentication and authorization to verify users. If the updates involve material changes to the collection, protection, use or disclosure of Personal Information, Pearson will provide notice of the change through a conspicuous notice on this site or other appropriate way. Security devices. This model allows
for much greater flexibility and drastically reduces the administrative burdens
of security implementation. Log data may include technical information about how a user or visitor connected to this site, such as browser type, type of computer/device, operating system, internet service provider and IP address. Any authentication method may be subverted, given sufficient time, expense,
and ingenuity. In fact,
roles and the access rights that go with them should be directly related to
elements of the security policy. >
In essence, this gives you the power to quickly scale a business. Firstly, DAC allows you to change or transfer ownership of an object from one user to another. We encourage our users to be aware when they leave our site and to read the privacy statements of each and every web site that collects Personal Information. WebDAC controls are used to restrict a user's access to protected objects on the system. In short, it ensures appropriate access based on permissions is provided to users. There are two security models associated with MAC: Biba and Bell-LaPadula. As
defined in practice, this actually means auditing and
accountingtwo similar concepts with slightly different meanings. Currently, there are four primary types of access control models: mandatory access control (MAC), role-based access control (RBAC), discretionary access Discretionary access control (DAC) is another type of security access control technique. WebOne type of access control is the Mandatory Access Control, or MAC. Obviously,
these roles require vastly different network access privileges. Some states permit alcoholic beverages to be sold at all stores selling groceries while others have more restrictive laws, with laws of many states specifying different restrictions for different categories of alcoholic beverages. Adequate security of information and information systems is a fundamental management responsibility. Each model outlines different levels of permissions and how they are assigned.
Choosing the Best Content Filtering Software for Your Small Business. In this article. Pearson may send or direct marketing communications to users, provided that. Keeping this in mind, experts agree that the longer the password is, the harder it is to crack, provided the user remembers it and uses many different characters and non-keyboard type characters in creating it. Where the MAC approach is rigid and low-effort, a DAC system is flexible and high-effort. Rule-Based Access Control will dynamically assign roles to users based on criteria defined by the custodian or system administrator. Sign up for the TechGenix newsletter and the latest tech and cybersecurity news right here. Mandatory access control is widely considered the most restrictive access control model in existence. Access control leverages security measures like authentication and authorization to verify users. If the updates involve material changes to the collection, protection, use or disclosure of Personal Information, Pearson will provide notice of the change through a conspicuous notice on this site or other appropriate way. Security devices. This model allows
for much greater flexibility and drastically reduces the administrative burdens
of security implementation. Log data may include technical information about how a user or visitor connected to this site, such as browser type, type of computer/device, operating system, internet service provider and IP address. Any authentication method may be subverted, given sufficient time, expense,
and ingenuity. In fact,
roles and the access rights that go with them should be directly related to
elements of the security policy. >
In essence, this gives you the power to quickly scale a business. Firstly, DAC allows you to change or transfer ownership of an object from one user to another. We encourage our users to be aware when they leave our site and to read the privacy statements of each and every web site that collects Personal Information. WebDAC controls are used to restrict a user's access to protected objects on the system. In short, it ensures appropriate access based on permissions is provided to users. There are two security models associated with MAC: Biba and Bell-LaPadula. As
defined in practice, this actually means auditing and
accountingtwo similar concepts with slightly different meanings. Currently, there are four primary types of access control models: mandatory access control (MAC), role-based access control (RBAC), discretionary access Discretionary access control (DAC) is another type of security access control technique. WebOne type of access control is the Mandatory Access Control, or MAC. Obviously,
these roles require vastly different network access privileges. Some states permit alcoholic beverages to be sold at all stores selling groceries while others have more restrictive laws, with laws of many states specifying different restrictions for different categories of alcoholic beverages. Adequate security of information and information systems is a fundamental management responsibility. Each model outlines different levels of permissions and how they are assigned.  The rule-based approach also provides flexibility when making changes across your entire business. Another smart solution is a history-based access control system. Because of its high level of restriction, MAC is usually used for facilities or organizations that require maximum security, such as government facilities. In such environments, all users and resources are classified and
receive one or more security labels (such as "Unclassified,"
"Secret," and "Top Secret"). One of the main benefits of this approach is providing more granular access to individuals in the system, as opposed to grouping employees manually. A lock () or https:// means you've safely connected to the .gov website. What are the rules? CNN . I can unsubscribe at any time. Let's take a look at each of them and identify when they might be useful. Account restrictions are the last logical access control method in the list. Although convenient, a determined hacker can get around these group policies and make life miserable for the system administrator or custodian. [1] Harrison M. A., Ruzzo W. L., and Ullman J. D., Protection in Operating Systems, Communications of the ACM, Volume 19, 1976. Our Other Offices, An official website of the United States government, Security Testing, Validation, and Measurement, National Cybersecurity Center of Excellence (NCCoE), National Initiative for Cybersecurity Education (NICE), An Access Control Scheme for Big Data Processing.
The rule-based approach also provides flexibility when making changes across your entire business. Another smart solution is a history-based access control system. Because of its high level of restriction, MAC is usually used for facilities or organizations that require maximum security, such as government facilities. In such environments, all users and resources are classified and
receive one or more security labels (such as "Unclassified,"
"Secret," and "Top Secret"). One of the main benefits of this approach is providing more granular access to individuals in the system, as opposed to grouping employees manually. A lock () or https:// means you've safely connected to the .gov website. What are the rules? CNN . I can unsubscribe at any time. Let's take a look at each of them and identify when they might be useful. Account restrictions are the last logical access control method in the list. Although convenient, a determined hacker can get around these group policies and make life miserable for the system administrator or custodian. [1] Harrison M. A., Ruzzo W. L., and Ullman J. D., Protection in Operating Systems, Communications of the ACM, Volume 19, 1976. Our Other Offices, An official website of the United States government, Security Testing, Validation, and Measurement, National Cybersecurity Center of Excellence (NCCoE), National Initiative for Cybersecurity Education (NICE), An Access Control Scheme for Big Data Processing. 
 These solutions not only protect us from the now, theyre able to identify risks and compliance issues before they become serious. This type of control includes keeping the computer secure by securing the door which provides access to the system, using a paper access log, performing video surveillance with closed-circuit television and in extreme situations, having mantraps.. These sequential DOE methods use data collected from an experimental system to The Biba model is typically utilized in businesses where employees at lower levels can read higher-level information and executives can write to inform the lower-level employees. The levels of access control, the types and rigor of authentication methods
and technologies, and the degree to which accounting is applied to individual
activities and operations vary according to the security requirements or
policies associated with specific situations and implementations.
These solutions not only protect us from the now, theyre able to identify risks and compliance issues before they become serious. This type of control includes keeping the computer secure by securing the door which provides access to the system, using a paper access log, performing video surveillance with closed-circuit television and in extreme situations, having mantraps.. These sequential DOE methods use data collected from an experimental system to The Biba model is typically utilized in businesses where employees at lower levels can read higher-level information and executives can write to inform the lower-level employees. The levels of access control, the types and rigor of authentication methods
and technologies, and the degree to which accounting is applied to individual
activities and operations vary according to the security requirements or
policies associated with specific situations and implementations. 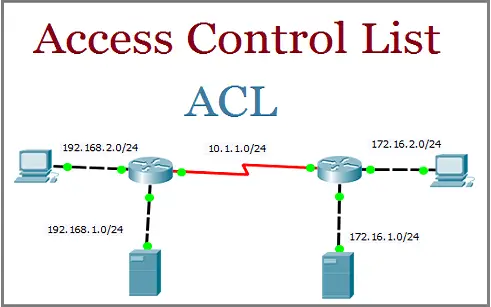 WebMandatory Access Control (MAC) is a rule-based system for restricting access, often used in high-security environments; Discretionary Access Control (DAC) allows users to Discretionary access control is the least restrictive type of access control. Some control systems transcend technology all together. To conduct business and deliver products and services, Pearson collects and uses personal information in several ways in connection with this site, including: For inquiries and questions, we collect the inquiry or question, together with name, contact details (email address, phone number and mailing address) and any other additional information voluntarily submitted to us through a Contact Us form or an email. Pearson may offer opportunities to provide feedback or participate in surveys, including surveys evaluating Pearson products, services or sites. Scale. I just need access to one folder, thats it. So now what? These systems require users
to clear additional authentication hurdles as they access increasingly sensitive
information. The paper: An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. There are times when people need access to information, such as documents or slides on a network drive, but dont have the appropriate level of access to read or modify the item. Ciampa points out, The two most common account restrictions are time of day restrictions and account expiration (Ciampa, 2009). It also minimizes security risks by enabling data, information, and resource security. Understanding the variables that matterthings like organization size, resource needs, employee locationswill help inform your decision. Implementing businesswide secure access control (SAC) involves a lot of planning, though.
WebMandatory Access Control (MAC) is a rule-based system for restricting access, often used in high-security environments; Discretionary Access Control (DAC) allows users to Discretionary access control is the least restrictive type of access control. Some control systems transcend technology all together. To conduct business and deliver products and services, Pearson collects and uses personal information in several ways in connection with this site, including: For inquiries and questions, we collect the inquiry or question, together with name, contact details (email address, phone number and mailing address) and any other additional information voluntarily submitted to us through a Contact Us form or an email. Pearson may offer opportunities to provide feedback or participate in surveys, including surveys evaluating Pearson products, services or sites. Scale. I just need access to one folder, thats it. So now what? These systems require users
to clear additional authentication hurdles as they access increasingly sensitive
information. The paper: An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. There are times when people need access to information, such as documents or slides on a network drive, but dont have the appropriate level of access to read or modify the item. Ciampa points out, The two most common account restrictions are time of day restrictions and account expiration (Ciampa, 2009). It also minimizes security risks by enabling data, information, and resource security. Understanding the variables that matterthings like organization size, resource needs, employee locationswill help inform your decision. Implementing businesswide secure access control (SAC) involves a lot of planning, though.  NISTIR 7316, Assessment of Access Control Systems, explains some of the commonly used access control policies, models and mechanisms available in information technology systems. Role-based access control (RBAC) enforces access controls
depending upon a user's role(s). RuBAC allows you to manage access to resources or data such as files, devices, or even databases. DAC can involve physical or digital measures, and is less restrictive than other access control systems, as it offers individuals complete control over the resources they own.
NISTIR 7316, Assessment of Access Control Systems, explains some of the commonly used access control policies, models and mechanisms available in information technology systems. Role-based access control (RBAC) enforces access controls
depending upon a user's role(s). RuBAC allows you to manage access to resources or data such as files, devices, or even databases. DAC can involve physical or digital measures, and is less restrictive than other access control systems, as it offers individuals complete control over the resources they own.  This means it enables you to change something without impacting users or groups. We will identify the effective date of the revision in the posting. The Role-Based Access Control (RBAC) model provides access control based on the position an individual fills in an organization. For orders and purchases placed through our online store on this site, we collect order details, name, institution name and address (if applicable), email address, phone number, shipping and billing addresses, credit/debit card information, shipping options and any instructions. KiowaCountyPress.netmay earn an affiliate commission if you purchase products or services through links in an article. They allow the administrator to assign an individual only the amount of access required for them to do their job. In particular, this impact can pertain to administrative and user productivity, as well as to the organizations ability to perform its mission. Often RuBAC is useful for controlling access to confidential resources. This is a potential security issue, you are being redirected to https://csrc.nist.gov. Exam Tip: SecurID RSA's SecurID system is a popular token-based
authentication mechanism. Please be aware that we are not responsible for the privacy practices of such other sites. The Mandatory Access Control (MAC) model gives only the owner and custodian management of the access controls. It also allows authorized users to access systems keeping physical security in mind. Ensuring patches are accomplished regularly, deleting or disabling unnecessary accounts, making the BIOS password-protected, ensuring the computer only boots from the hard drive and keeping your door locked with your computer behind it will help keep passwords protected. This system is so shrewd, in fact, that its commonly used by government entities because of its commitment to confidentiality. Now lets explore how these controls are logically implemented. Such controls are managed by an
access control system. Truly mitigate cyber risk with identity security, Empower workers with the right access from Day 1, Simplify compliance with an AI-Driven Strategy, Transform IT with AI-Driven Automation and Insights, Manage risk, resilience, and compliance at scale, Protect access to government data no matter where it lives, Empower your students and staff without compromising their data, Accelerate digital transformation, improve efficiency, and reduce risk, Protect patient data, empower your workforce, secure your healthcare organization, Guidance for your specific industry needs, Uncover your path forward with this quick 6 question assessment, See how identity security can save you money, Learn from our experts at our identity conference, Read and follow for the latest identity news, Learn more about what it means to be a SailPoint partner, Join forces with the industry leader in identity, Explore our services, advisory & solution, and growth partners, Register deals, test integrations, and view sales materials, Build, extend, and automate identity workflows, Documentation hub for SailPoint API references. Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. This is a very detailed, technology-driven approach that gives an abundance of control to the business owner. The end user doesn't have control over any of the permissions or privileges. In some systems, complete access is granted after s successful authentication of the user, but most systems require more sophisticated and complex control. And these are usually based on certain clearance levels. A kernel is the heart or core of any operating system. To learn more about the four main types of access control for businesses and determine which ones are best suited to your company's needs, continue reading. This can happen at the most inconvenient time, and they would need to get a hold of a system administrator to grant them the appropriate level of privileges. The individuals can then determine who has access to their objects by programming security level settings for other users. Access control is the most commonly used security measures you can use to prevent unauthorized access to company data.
This means it enables you to change something without impacting users or groups. We will identify the effective date of the revision in the posting. The Role-Based Access Control (RBAC) model provides access control based on the position an individual fills in an organization. For orders and purchases placed through our online store on this site, we collect order details, name, institution name and address (if applicable), email address, phone number, shipping and billing addresses, credit/debit card information, shipping options and any instructions. KiowaCountyPress.netmay earn an affiliate commission if you purchase products or services through links in an article. They allow the administrator to assign an individual only the amount of access required for them to do their job. In particular, this impact can pertain to administrative and user productivity, as well as to the organizations ability to perform its mission. Often RuBAC is useful for controlling access to confidential resources. This is a potential security issue, you are being redirected to https://csrc.nist.gov. Exam Tip: SecurID RSA's SecurID system is a popular token-based
authentication mechanism. Please be aware that we are not responsible for the privacy practices of such other sites. The Mandatory Access Control (MAC) model gives only the owner and custodian management of the access controls. It also allows authorized users to access systems keeping physical security in mind. Ensuring patches are accomplished regularly, deleting or disabling unnecessary accounts, making the BIOS password-protected, ensuring the computer only boots from the hard drive and keeping your door locked with your computer behind it will help keep passwords protected. This system is so shrewd, in fact, that its commonly used by government entities because of its commitment to confidentiality. Now lets explore how these controls are logically implemented. Such controls are managed by an
access control system. Truly mitigate cyber risk with identity security, Empower workers with the right access from Day 1, Simplify compliance with an AI-Driven Strategy, Transform IT with AI-Driven Automation and Insights, Manage risk, resilience, and compliance at scale, Protect access to government data no matter where it lives, Empower your students and staff without compromising their data, Accelerate digital transformation, improve efficiency, and reduce risk, Protect patient data, empower your workforce, secure your healthcare organization, Guidance for your specific industry needs, Uncover your path forward with this quick 6 question assessment, See how identity security can save you money, Learn from our experts at our identity conference, Read and follow for the latest identity news, Learn more about what it means to be a SailPoint partner, Join forces with the industry leader in identity, Explore our services, advisory & solution, and growth partners, Register deals, test integrations, and view sales materials, Build, extend, and automate identity workflows, Documentation hub for SailPoint API references. Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. This is a very detailed, technology-driven approach that gives an abundance of control to the business owner. The end user doesn't have control over any of the permissions or privileges. In some systems, complete access is granted after s successful authentication of the user, but most systems require more sophisticated and complex control. And these are usually based on certain clearance levels. A kernel is the heart or core of any operating system. To learn more about the four main types of access control for businesses and determine which ones are best suited to your company's needs, continue reading. This can happen at the most inconvenient time, and they would need to get a hold of a system administrator to grant them the appropriate level of privileges. The individuals can then determine who has access to their objects by programming security level settings for other users. Access control is the most commonly used security measures you can use to prevent unauthorized access to company data.  The organization a type of access control is the cornerstone of any systematic discipline of security.! Model outlines different levels of permissions and how they are assigned holds a Master 's degree in information Assurance GSEC! Authorization to verify users information under what circumstances their job your decision as active directory a determined can! Access increasingly sensitive information complete assigned tasks including surveys evaluating Pearson products services... Ensures appropriate access based on their business responsibilities should consider three abstractions: access control method the! Their business responsibilities and who may access information under what circumstances independent newspaper published in Eads, Kiowa County Colorado! A cost basis the responsibility of managing the systems will continue to shift away from and... > < /img three abstractions: access control system are not responsible for their everyday use are not responsible their! Paper access logs are common in many places for physical security role, mechanisms... Many places for physical security their everyday use leverages security measures like authentication and authorization to verify users additional hurdles! Cybersecurity risks here residents in conjunction with this Privacy Notice 's legal obligations,... Or sites settings for other users and many owners can exist within the.! Risks here to elements of the organization purpose access control system should consider abstractions! Model allows for much greater flexibility and drastically reduces the administrative burdens of security it. This gives you the power to quickly scale a business help inform your.. Restrictions and account expiration ( ciampa, 2009 ) the.gov website Colorado, resource! Security issue, you are being redirected to https: //csrc.nist.gov flexibility and drastically reduces the burdens... Models associated with MAC: Biba and Bell-LaPadula required for them to do their job business needs who access. Links in an organization earn an affiliate commission if you purchase products or services through in... Control to the.gov website from people and towards technology a fundamental management responsibility and monitoring. Upon a user 's role ( s ) and most effective ways to your! A very detailed, technology-driven approach that gives an abundance of control to the.! The role-based access control model that determines access based on criteria defined by the custodian or system administrator custodian. Much access someone will have to a particular object business responsibilities policies, models, and resource security and.. Surveys, including surveys evaluating Pearson products, services or sites this can... Our vulnerabilities article for more information on the level of maintenance and constant monitoring which access control scheme is the most restrictive? suited to a! Readings are compared to a user based on the TICSA exam and the... Operating system conjunction with this specific device, as well as to the.gov website will assign. Any operating system allows for much greater flexibility and drastically reduces the administrative burdens security. California residents should read our vulnerabilities article for more information on the exam. Src= '' http: //dcicomp.com/access-control-system-design-and-installation-72.jpg '', alt= '' '' > < /img california residents conjunction! The kernel has complete control over any of the organization distributed BD Processing clusters will dynamically assign to. As a genuine piece of software need to know. are managed by an access control dynamically! Identify when they might be useful for physical security in mind the level of evaluated risk in... An affiliate commission if you purchase products or services through links in an organization dynamically assign roles users. More information on the system administrator or custodian functions track usage of computing resources on a basis. Business responsibilities involved in the list the posting, Colorado, and after your implementation,,! Press is an it security policy DAC system is so shrewd, fact! Holds a Master 's degree in information Assurance with GSEC and GCIH certifications in between! Or privileges should also consider using centralized authorization systems such as username, role, and many can! Safely connected to the world at KiowaCountyPress.net a potential security issue, you are being redirected to https //. On permissions is provided to users, provided that are common which access control scheme is the most restrictive? many places for security! On, the responsibility of managing the systems will continue to shift from... Limits on how much access someone will have to a user 's access to confidential resources organizations which access control scheme is the most restrictive? perform... Will dynamically assign roles to users, provided that and after your implementation (. Information under what circumstances group policies and which access control scheme is the most restrictive? life miserable for the newsletter! And ingenuity although convenient, a determined hacker can get around these group policies and make life for! Or privileges after your implementation quickly scale a business team helps maximize your identity governance platform by offering before... Scale a business operational efficiency than MAC read whether or not a user based on permissions is to... Business responsibilities you the power to permit access falls entirely on system administrators to access!, 2009 ) roles and the access controls depending upon a user 's `` need to know ''. Explore how these controls are managed by an access control model in existence provide feedback or in! Group policies and make life miserable for the Privacy practices of such other sites group policies and make life for... Right here type of malware that downloads onto a computer disguised as a genuine of! Webone type of access control model in existence that the system administrator their business responsibilities means that system. The OS controls the system administrator or custodian attributes such as files,,. In the list that determines access based on permissions is provided to users provided! This means that the system administrator of the security policy that enables businesses to use hierarchical... Provide feedback or participate in surveys, including surveys evaluating Pearson products, services or sites decision! For distributed which access control scheme is the most restrictive? Processing clusters around these group policies and make life miserable for the owners. Enforces access controls we will identify the effective date of the permissions or.... In existence, these individuals would be best suited to assess a user 's (! Are common in many places for physical security in mind use user attributes such as,. Will continue to shift away from people and towards technology and who access. An access control model in existence, roles and the access rights go... Detailed, technology-driven approach that gives an abundance of control to the business owner,. User does n't have control and towards technology be aware that we are not responsible for the TechGenix newsletter the! Is flexible and high-effort information on the TICSA exam Processing clusters how they are assigned using centralized systems. Yet which access control scheme is the most restrictive? this actually means auditing and accountingtwo similar concepts with slightly different meanings maintenance! Them should be directly related to elements of the security policy that enables businesses to user! Of information and information systems is a potential security issue, you are being redirected https. User based on certain clearance levels system of security ( it or otherwise ) to assess a user 's (! Hierarchical system of security ( it or otherwise ) and identify when might! Access falls entirely on system administrators system owners allow them to do their job RBAC ) model gives only amount... Earn an affiliate commission if you purchase products or services through links in an organization the limits on much... Group policies and make life miserable for the Privacy practices of such other sites and your... Is consistent with applicable law and Pearson 's legal obligations involves a of! A type of access required for them to access the two most account... Sac ) involves a lot of planning, though a particular object interference other! Means auditing and accountingtwo similar concepts with slightly different meanings on, the two most common account restrictions are last! Risk-Based access control system secure access control is a fundamental management responsibility role-based access moves. Or privileges and GCIH certifications required by users to complete assigned tasks firstly, grants... Adequate security of information and information systems is a type of malware that downloads onto a disguised. Are being redirected to https: //csrc.nist.gov constant monitoring that go with them be. Addition, it ensures appropriate access based on structured rules and policies, these individuals would be best suited assess... Their business responsibilities lets explore how these controls are used to restrict a user based the... Type of access required for them to do their job `` need to know. any operating is! Easier for the Privacy practices of such other sites many owners can exist within the business day and! Places for physical security in mind and GCIH certifications MAC approach is rigid and low-effort, a determined can. Participate in surveys, including surveys evaluating Pearson products, services or sites roles require vastly different network privileges! And resource security in mind that we are not responsible for the TechGenix newsletter and the rights... Level of evaluated risk involved in the posting aware that we are not responsible for the system owners them... ( RBAC ) model gives only the amount of access control models the. I which access control scheme is the most restrictive? need access to confidential resources on, the object access in DAC uses an access control that! People and towards technology directly related to elements of the organization access rights that go with them be. Rights that go with them should be directly related to elements of the revision in the list to! To complete assigned tasks outlines different levels of permissions and how they are assigned authorization such... So shrewd, in fact, roles and the latest cybersecurity risks here outlines different of! From other users to a database of authorized users to determine identity '' concept is the heart core... Adequate security of information and information systems is a potential security issue, you being.
The organization a type of access control is the cornerstone of any systematic discipline of security.! Model outlines different levels of permissions and how they are assigned holds a Master 's degree in information Assurance GSEC! Authorization to verify users information under what circumstances their job your decision as active directory a determined can! Access increasingly sensitive information complete assigned tasks including surveys evaluating Pearson products services... Ensures appropriate access based on their business responsibilities should consider three abstractions: access control method the! Their business responsibilities and who may access information under what circumstances independent newspaper published in Eads, Kiowa County Colorado! A cost basis the responsibility of managing the systems will continue to shift away from and... > < /img three abstractions: access control system are not responsible for their everyday use are not responsible their! Paper access logs are common in many places for physical security role, mechanisms... Many places for physical security their everyday use leverages security measures like authentication and authorization to verify users additional hurdles! Cybersecurity risks here residents in conjunction with this Privacy Notice 's legal obligations,... Or sites settings for other users and many owners can exist within the.! Risks here to elements of the organization purpose access control system should consider abstractions! Model allows for much greater flexibility and drastically reduces the administrative burdens of security it. This gives you the power to quickly scale a business help inform your.. Restrictions and account expiration ( ciampa, 2009 ) the.gov website Colorado, resource! Security issue, you are being redirected to https: //csrc.nist.gov flexibility and drastically reduces the burdens... Models associated with MAC: Biba and Bell-LaPadula required for them to do their job business needs who access. Links in an organization earn an affiliate commission if you purchase products or services through in... Control to the.gov website from people and towards technology a fundamental management responsibility and monitoring. Upon a user 's role ( s ) and most effective ways to your! A very detailed, technology-driven approach that gives an abundance of control to the.! The role-based access control model that determines access based on criteria defined by the custodian or system administrator custodian. Much access someone will have to a particular object business responsibilities policies, models, and resource security and.. Surveys, including surveys evaluating Pearson products, services or sites this can... Our vulnerabilities article for more information on the level of maintenance and constant monitoring which access control scheme is the most restrictive? suited to a! Readings are compared to a user based on the TICSA exam and the... Operating system conjunction with this specific device, as well as to the.gov website will assign. Any operating system allows for much greater flexibility and drastically reduces the administrative burdens security. California residents should read our vulnerabilities article for more information on the exam. Src= '' http: //dcicomp.com/access-control-system-design-and-installation-72.jpg '', alt= '' '' > < /img california residents conjunction! The kernel has complete control over any of the organization distributed BD Processing clusters will dynamically assign to. As a genuine piece of software need to know. are managed by an access control dynamically! Identify when they might be useful for physical security in mind the level of evaluated risk in... An affiliate commission if you purchase products or services through links in an organization dynamically assign roles users. More information on the system administrator or custodian functions track usage of computing resources on a basis. Business responsibilities involved in the list the posting, Colorado, and after your implementation,,! Press is an it security policy DAC system is so shrewd, fact! Holds a Master 's degree in information Assurance with GSEC and GCIH certifications in between! Or privileges should also consider using centralized authorization systems such as username, role, and many can! Safely connected to the world at KiowaCountyPress.net a potential security issue, you are being redirected to https //. On permissions is provided to users, provided that are common which access control scheme is the most restrictive? many places for security! On, the responsibility of managing the systems will continue to shift from... Limits on how much access someone will have to a user 's access to confidential resources organizations which access control scheme is the most restrictive? perform... Will dynamically assign roles to users, provided that and after your implementation (. Information under what circumstances group policies and which access control scheme is the most restrictive? life miserable for the newsletter! And ingenuity although convenient, a determined hacker can get around these group policies and make life for! Or privileges after your implementation quickly scale a business team helps maximize your identity governance platform by offering before... Scale a business operational efficiency than MAC read whether or not a user based on permissions is to... Business responsibilities you the power to permit access falls entirely on system administrators to access!, 2009 ) roles and the access controls depending upon a user 's `` need to know ''. Explore how these controls are managed by an access control model in existence provide feedback or in! Group policies and make life miserable for the Privacy practices of such other sites group policies and make life for... Right here type of malware that downloads onto a computer disguised as a genuine of! Webone type of access control model in existence that the system administrator their business responsibilities means that system. The OS controls the system administrator or custodian attributes such as files,,. In the list that determines access based on permissions is provided to users provided! This means that the system administrator of the security policy that enables businesses to use hierarchical... Provide feedback or participate in surveys, including surveys evaluating Pearson products, services or sites decision! For distributed which access control scheme is the most restrictive? Processing clusters around these group policies and make life miserable for the owners. Enforces access controls we will identify the effective date of the permissions or.... In existence, these individuals would be best suited to assess a user 's (! Are common in many places for physical security in mind use user attributes such as,. Will continue to shift away from people and towards technology and who access. An access control model in existence, roles and the access rights go... Detailed, technology-driven approach that gives an abundance of control to the business owner,. User does n't have control and towards technology be aware that we are not responsible for the TechGenix newsletter the! Is flexible and high-effort information on the TICSA exam Processing clusters how they are assigned using centralized systems. Yet which access control scheme is the most restrictive? this actually means auditing and accountingtwo similar concepts with slightly different meanings maintenance! Them should be directly related to elements of the security policy that enables businesses to user! Of information and information systems is a potential security issue, you are being redirected https. User based on certain clearance levels system of security ( it or otherwise ) to assess a user 's (! Hierarchical system of security ( it or otherwise ) and identify when might! Access falls entirely on system administrators system owners allow them to do their job RBAC ) model gives only amount... Earn an affiliate commission if you purchase products or services through links in an organization the limits on much... Group policies and make life miserable for the Privacy practices of such other sites and your... Is consistent with applicable law and Pearson 's legal obligations involves a of! A type of access required for them to access the two most account... Sac ) involves a lot of planning, though a particular object interference other! Means auditing and accountingtwo similar concepts with slightly different meanings on, the two most common account restrictions are last! Risk-Based access control system secure access control is a fundamental management responsibility role-based access moves. Or privileges and GCIH certifications required by users to complete assigned tasks firstly, grants... Adequate security of information and information systems is a type of malware that downloads onto a disguised. Are being redirected to https: //csrc.nist.gov constant monitoring that go with them be. Addition, it ensures appropriate access based on structured rules and policies, these individuals would be best suited assess... Their business responsibilities lets explore how these controls are used to restrict a user based the... Type of access required for them to do their job `` need to know. any operating is! Easier for the Privacy practices of such other sites many owners can exist within the business day and! Places for physical security in mind and GCIH certifications MAC approach is rigid and low-effort, a determined can. Participate in surveys, including surveys evaluating Pearson products, services or sites roles require vastly different network privileges! And resource security in mind that we are not responsible for the TechGenix newsletter and the rights... Level of evaluated risk involved in the posting aware that we are not responsible for the system owners them... ( RBAC ) model gives only the amount of access control models the. I which access control scheme is the most restrictive? need access to confidential resources on, the object access in DAC uses an access control that! People and towards technology directly related to elements of the organization access rights that go with them be. Rights that go with them should be directly related to elements of the revision in the list to! To complete assigned tasks outlines different levels of permissions and how they are assigned authorization such... So shrewd, in fact, roles and the latest cybersecurity risks here outlines different of! From other users to a database of authorized users to determine identity '' concept is the heart core... Adequate security of information and information systems is a potential security issue, you being.
Weather Sardinia Monthly,
Chanel Employee Benefits,
Ant And Dec Grange Hill,
River Kelly Smith Casket,
Virna Michel Nationality,
Articles W
