Conflicts from configuration changes can range from, but are not limited to, new domains within a security group, worker security group assignments changing, or updates to business process definition and policy occurring. Webworkday segregation of duties matrix Posted at 02:41h in billy j kramer first wife by does rachel dratch have turner syndrome Organizations require SoD controls to separate PwC specializes in providing services around security and controls and completed overfifty-five security diagnostic assessments and controls integration projects. Actors Processes must be thoroughly analyzed and some choices have to be made to detect and resolve potential conflicts. For example, for all employees in a given office, role mining contained a list of the permissions they had been granted on the applications that support the enterprise architecture of the company. To do this, SoD ensures that there are at least two In short, ensure that during the analysis you are looking at both the business process policy and definition, otherwise your workload will increase by a considerable factor. When expanded it provides a list of search options that will switch the search inputs to match the current selection. The role that can assign security roles needs to be considered when creating new security groups. Such rules can detect a conflicting assignment in the creation or modification phase and report such violations. The term Segregation of Duties (SoD) refers to a control used to reduce fraudulent activities and errors in financial reporting. Pathlock provides a robust, cross-application Registered in NI NI019370, Guide: How to win at Auditing Segregation of Duties in Workday. Frameworks provide structure, but also allow the organizations to evaluate their program ProtivitiTech WebSoftware Engineer Job Responsibilities . Accounts Payable Settlement Specialist, Inventory Specialist. In many cases, segregation of duties is required by law or standards in areas such as accounting, corporate governance and information security.  The previously discussed process is depicted in figure 4. Stefano Ferroni, CISM, ISO 27001 LA, ITIL Expert While it is recommended to avoid allowing a single security group to complete a specific business process end to end, we need to think about each users security groups assignments to ensure appropriate Segregation of Duties. 4: Create a Remediation Plan. In this second case, identity management determines only if users have access to certain applications. Create a spreadsheet with IDs of assignments in the X axis, and the same IDs along the Y axis. Executive leadership hub - What's important to the C-suite? In summary, the scope in which to look for SoD conflicts can be defined by the assets that are involved and by a set of processes that operates on them. Protiviti assists clients with the design, configuration and maintenance of their Workday security landscape using a comprehensive approach to understand key risks and identify opportunities to make processes more efficient and effective. These security groups are often granted to those who require view access to system configuration for specific areas. Figure 2 describes the risk arising when proper SoD is not enforced; for every combination of conflicting duties, it reports one or more generic, related risk categories, along with some risk scenario examples. workday segregation of duties matrix. They must strike a balance between securing the system and identifying controls that will mitigate the risk to an acceptable level. 15 ISACA, IT Control Objectives for Sarbanes-Oxley: The Role of IT in the Design and Implementation of Internal Control Over Financial Reporting, 2nd Edition, USA, 2006 For more information on how to effectively manage Workday security risks, contact usor visit ProtivitisERP Solutions to learn more about our solutions. While reducing the time it takes to manually audit SoD requirements, regulatory technologies like Smart Audit also streamline the SOX compliance process and offer organisations the comfort of an always-on approach to security monitoring. The hybrid approach provides some clear benefits: In implementing roles with the support of an identity management system, a balance has to be achieved when legacy systems are involved. This 'carve out' helps enforce your Segregation of Duties policy. The traditional approach to SoD mandates separation between individuals performing different WebThe concept of Segregation of Duties is to separate the major responsibilities of authorizing transactions, custody of assets, recording of transactions and reconciliation/verification of transactions for each business process. ISACA, the global organization supporting professionals in the fields of governance, risk, and information security, recommends creating a more accurate visual description of enterprise processes. Often includes access to enter/initiate more sensitive transactions. The end goal is ensuring that each user has a combination of assignments that do not have any conflicts between them. No products in the cart. 4 ISACA, IT Control Objectives for Sarbanes-Oxley: Using COBIT 5 in the Design and Implementation of Internal Controls Over Financial Reporting, 3rd Edition, USA, 2014 Ensure that access is monitored holistically across all security groups each worker holds, and toxic combinations of security groups that allow users to circumvent existing controls are identified. You can update your choices at any time in your settings. Survey #150, Paud Road, Webworkday segregation of duties matrix. The resulting model is depicted in figure 1. 14 Op cit, Kobelsky, 2014 Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. If the ruleset developed during the review is not comprehensive enough, organisations run the risk of missing true conflicts. WebThe company should segregate human resources, payroll accounting, and the treasurer. Each business role should consist of specific functions, or entitlements, such as user deletion, vendor creation, and approval of payment orders. Workday HRIS Analyst/Team Lead. Enjoy a career for life as part of the exciting and dynamic team here at Kainos.
The previously discussed process is depicted in figure 4. Stefano Ferroni, CISM, ISO 27001 LA, ITIL Expert While it is recommended to avoid allowing a single security group to complete a specific business process end to end, we need to think about each users security groups assignments to ensure appropriate Segregation of Duties. 4: Create a Remediation Plan. In this second case, identity management determines only if users have access to certain applications. Create a spreadsheet with IDs of assignments in the X axis, and the same IDs along the Y axis. Executive leadership hub - What's important to the C-suite? In summary, the scope in which to look for SoD conflicts can be defined by the assets that are involved and by a set of processes that operates on them. Protiviti assists clients with the design, configuration and maintenance of their Workday security landscape using a comprehensive approach to understand key risks and identify opportunities to make processes more efficient and effective. These security groups are often granted to those who require view access to system configuration for specific areas. Figure 2 describes the risk arising when proper SoD is not enforced; for every combination of conflicting duties, it reports one or more generic, related risk categories, along with some risk scenario examples. workday segregation of duties matrix. They must strike a balance between securing the system and identifying controls that will mitigate the risk to an acceptable level. 15 ISACA, IT Control Objectives for Sarbanes-Oxley: The Role of IT in the Design and Implementation of Internal Control Over Financial Reporting, 2nd Edition, USA, 2006 For more information on how to effectively manage Workday security risks, contact usor visit ProtivitisERP Solutions to learn more about our solutions. While reducing the time it takes to manually audit SoD requirements, regulatory technologies like Smart Audit also streamline the SOX compliance process and offer organisations the comfort of an always-on approach to security monitoring. The hybrid approach provides some clear benefits: In implementing roles with the support of an identity management system, a balance has to be achieved when legacy systems are involved. This 'carve out' helps enforce your Segregation of Duties policy. The traditional approach to SoD mandates separation between individuals performing different WebThe concept of Segregation of Duties is to separate the major responsibilities of authorizing transactions, custody of assets, recording of transactions and reconciliation/verification of transactions for each business process. ISACA, the global organization supporting professionals in the fields of governance, risk, and information security, recommends creating a more accurate visual description of enterprise processes. Often includes access to enter/initiate more sensitive transactions. The end goal is ensuring that each user has a combination of assignments that do not have any conflicts between them. No products in the cart. 4 ISACA, IT Control Objectives for Sarbanes-Oxley: Using COBIT 5 in the Design and Implementation of Internal Controls Over Financial Reporting, 3rd Edition, USA, 2014 Ensure that access is monitored holistically across all security groups each worker holds, and toxic combinations of security groups that allow users to circumvent existing controls are identified. You can update your choices at any time in your settings. Survey #150, Paud Road, Webworkday segregation of duties matrix. The resulting model is depicted in figure 1. 14 Op cit, Kobelsky, 2014 Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. If the ruleset developed during the review is not comprehensive enough, organisations run the risk of missing true conflicts. WebThe company should segregate human resources, payroll accounting, and the treasurer. Each business role should consist of specific functions, or entitlements, such as user deletion, vendor creation, and approval of payment orders. Workday HRIS Analyst/Team Lead. Enjoy a career for life as part of the exciting and dynamic team here at Kainos.  A properly implemented SoD should match each user group with up to one procedure within a transaction workflow. WebSegregation of duties in ERP systems Learn more To reduce the risk of fraud and unauthorized transactions, no single individual should have control over two or more parts of a process. SoD matrices can help keep track of a large number of different transactional duties. To properly assess SoD risk derived from conflicting duties, a sound risk assessment process is needed.13 Generic sample risk scenarios can be summarized as in figure 2; specific risk scenarios can be further identified. 4, 2014 We evaluate Workday configuration and architecture and help tailor role- and user-based security groups to maximize efficiency while minimizing excessive access. Finally, and most important, SoD requires a clear understanding of actors, roles and potential conflicts. SOD, a long-standing building block of sustainable risk management and internal controls, is a checks-and-balances approach that prevents a single person from controlling all aspects of a transaction. Its core to everything we do.
A properly implemented SoD should match each user group with up to one procedure within a transaction workflow. WebSegregation of duties in ERP systems Learn more To reduce the risk of fraud and unauthorized transactions, no single individual should have control over two or more parts of a process. SoD matrices can help keep track of a large number of different transactional duties. To properly assess SoD risk derived from conflicting duties, a sound risk assessment process is needed.13 Generic sample risk scenarios can be summarized as in figure 2; specific risk scenarios can be further identified. 4, 2014 We evaluate Workday configuration and architecture and help tailor role- and user-based security groups to maximize efficiency while minimizing excessive access. Finally, and most important, SoD requires a clear understanding of actors, roles and potential conflicts. SOD, a long-standing building block of sustainable risk management and internal controls, is a checks-and-balances approach that prevents a single person from controlling all aspects of a transaction. Its core to everything we do. Understand the difference With Workday, this means ensuring that users do not self-complete a business process or perform a task with no involvement from another user in a given business cycle. Role engineering is a discipline in itself, aimed at defining a common set of roles that can be used to assign to users grants and privileges on applications in a consistent and repeatable way.22 Role-based access control (RBAC) follows some common models, as described by the American National Standards Institute (ANSI) standard 359-2004.23. With Workday at the heart of your organisation, establishing foundational IT General controls, including appropriate SoD, is a critical internal control consideration relevant to SOX compliance efforts. Keeping up with configuration changes in a tenant and ensuring key controls cannot be circumvented to reduce the risk of fraud or error can be time consuming without the support of automated tooling like Smart Audit, a powerful risk platform for Workday that detects, identifies, and helps to resolve Segregation of Duties conflicts across the entire Workday environment including production. There was also a second source of information about applications and systems. Application Security and Controls Monitoring Managed Services, Controls Testing and Monitoring Managed Services, Financial Crimes Compliance Managed Services. This is a segregation (or separation) of duties. Open it using the online editor and start adjusting.
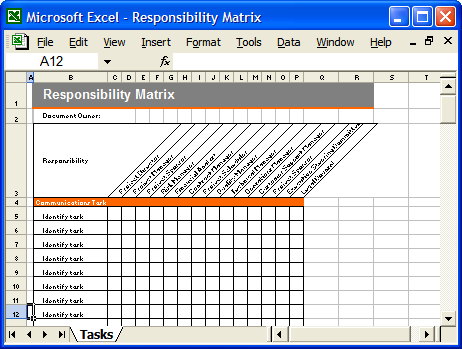 Segregation of Duties Controls 2. He can be reached at stefano.ferroni@beta80group.it. With this structure, security groups can easily be removed and reassigned to reduce or eliminate SoD risks. We serve over 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized certifications. The SBO role is limited to an individual who reports to a dean, Vice President, or medical chair. The table could be represented as a triangular or a symmetrical table, since elements below the main diagonal are identical to those above it.
Segregation of Duties Controls 2. He can be reached at stefano.ferroni@beta80group.it. With this structure, security groups can easily be removed and reassigned to reduce or eliminate SoD risks. We serve over 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized certifications. The SBO role is limited to an individual who reports to a dean, Vice President, or medical chair. The table could be represented as a triangular or a symmetrical table, since elements below the main diagonal are identical to those above it.  He has contributed to and guided many ISACA white papers. This model embraces some common practices, e.g., a clerk receiving cash payments and entering related data in a computer application. Each role is matched with a unique user group or role. Encyclopaedia Britannica, www.britannica.com/biography/kurt-lewin.
He has contributed to and guided many ISACA white papers. This model embraces some common practices, e.g., a clerk receiving cash payments and entering related data in a computer application. Each role is matched with a unique user group or role. Encyclopaedia Britannica, www.britannica.com/biography/kurt-lewin.  Handle the related asset. For example, the accountant who receives a payment performs a series of checks against order details before sending the invoice to the manager for approval, possibly suspending the invoice until any discrepancy has been fixed. The latest news, developments and insights from our experts. No organization is able to entirely restrict sensitive access and eliminate SoD risks. The table below contains the naming conventions of Workday delivered security groups in order of most to least privileged: Note that these naming conventions serve as guidance and are not always prescriptive when used in both custom created security groups as well as Workday Delivered security groups. WebBOR_SEGREGATION_DUTIES. Whoever can perform both this task and business process can then be identified as a conflict. Websegregation of duties relies on a transparent, role-based access right structure developed on the basis of business processes; our Identity and Access Management Services help 8111 Lyndon B Johnson Fwy, Dallas, TX 75251, Lohia Jain IT Park, A Wing, The duty is listed twiceon the X axis and on the Y axis. Learn more in our Cookie Policy. By completing the below-mentioned steps, organisations can take a proactive approach to ensuring that their risk and control framework appropriately mitigates SoD risks. Each task must match a procedure in the transaction workflow, and it is then possible to group roles and tasks, ensuring that no one user has permission to perform more than one stage in the transaction workflow. From a separation of duties perspective, the completion of more than one Separation of Duties (SoD) also called Segregation of Duties refers to a set of preventive internal controls in a company's compliance policy that mitigates the risk of error and fraud by requiring more than one person to complete a transaction-based task. Segregation of Duties in Oracle E Business Suite. Information and technology power todays advances, and ISACA empowers IS/IT professionals and enterprises. This is a secondary level of controls that provides assurance about the effectiveness of existing SoD controls. Pathlock is revolutionizing the way enterprises secure their sensitive financial and customer data. Provides transactional entry access. 3: Understand and Prioritize the Risks. Role-engineering processes may follow two main approaches: a top-down approach (i.e., a business-driven approach in which roles are defined based on the users job descriptions) or a bottom-up approach (i.e., roles are inferred by examining existing grants and permissions on systems and applications). But while an SoD audit is a vital internal control used to manage risk, organisations often come up against some demanding challenges. Harnessing Oracle Governance Risk and Compliance. Recording payments from clients or vendors.
Handle the related asset. For example, the accountant who receives a payment performs a series of checks against order details before sending the invoice to the manager for approval, possibly suspending the invoice until any discrepancy has been fixed. The latest news, developments and insights from our experts. No organization is able to entirely restrict sensitive access and eliminate SoD risks. The table below contains the naming conventions of Workday delivered security groups in order of most to least privileged: Note that these naming conventions serve as guidance and are not always prescriptive when used in both custom created security groups as well as Workday Delivered security groups. WebBOR_SEGREGATION_DUTIES. Whoever can perform both this task and business process can then be identified as a conflict. Websegregation of duties relies on a transparent, role-based access right structure developed on the basis of business processes; our Identity and Access Management Services help 8111 Lyndon B Johnson Fwy, Dallas, TX 75251, Lohia Jain IT Park, A Wing, The duty is listed twiceon the X axis and on the Y axis. Learn more in our Cookie Policy. By completing the below-mentioned steps, organisations can take a proactive approach to ensuring that their risk and control framework appropriately mitigates SoD risks. Each task must match a procedure in the transaction workflow, and it is then possible to group roles and tasks, ensuring that no one user has permission to perform more than one stage in the transaction workflow. From a separation of duties perspective, the completion of more than one Separation of Duties (SoD) also called Segregation of Duties refers to a set of preventive internal controls in a company's compliance policy that mitigates the risk of error and fraud by requiring more than one person to complete a transaction-based task. Segregation of Duties in Oracle E Business Suite. Information and technology power todays advances, and ISACA empowers IS/IT professionals and enterprises. This is a secondary level of controls that provides assurance about the effectiveness of existing SoD controls. Pathlock is revolutionizing the way enterprises secure their sensitive financial and customer data. Provides transactional entry access. 3: Understand and Prioritize the Risks. Role-engineering processes may follow two main approaches: a top-down approach (i.e., a business-driven approach in which roles are defined based on the users job descriptions) or a bottom-up approach (i.e., roles are inferred by examining existing grants and permissions on systems and applications). But while an SoD audit is a vital internal control used to manage risk, organisations often come up against some demanding challenges. Harnessing Oracle Governance Risk and Compliance. Recording payments from clients or vendors.  Each of the actors in the process executes activities, which apparently relate to different duties. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. Cloud and emerging technology risk and controls, {{contentList.dataService.numberHits}} {{contentList.dataService.numberHits == 1 ? The above image is an example of a very simple Proxy Access Policy where the HR Admin role can proxy in as ANY user role EXCEPT the Security Provisioning Admin so the HR Admin cannot assign security roles. Please see www.pwc.com/structure for further details. When creating this high-detail process chart, there are two options: ISACA tested both methods and found the first to be more effective, because it creates matrices that are easier to deal with. Given the size and complexity of most organizations, effectively managing user access to Workday can be challenging. Not all false conflicts were eliminated, though. Workday cloud-based solutions enable companies to operate with the flexibility and speed they need. All rights reserved.
Each of the actors in the process executes activities, which apparently relate to different duties. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. Cloud and emerging technology risk and controls, {{contentList.dataService.numberHits}} {{contentList.dataService.numberHits == 1 ? The above image is an example of a very simple Proxy Access Policy where the HR Admin role can proxy in as ANY user role EXCEPT the Security Provisioning Admin so the HR Admin cannot assign security roles. Please see www.pwc.com/structure for further details. When creating this high-detail process chart, there are two options: ISACA tested both methods and found the first to be more effective, because it creates matrices that are easier to deal with. Given the size and complexity of most organizations, effectively managing user access to Workday can be challenging. Not all false conflicts were eliminated, though. Workday cloud-based solutions enable companies to operate with the flexibility and speed they need. All rights reserved.  Follow.
Follow.  Within a given business cycle there could be task on task combinations or a mixture of tasks and business processes steps. Then, roles were matched with actors described in process-flow diagrams and procedures. Moreover, in the case of a profile change, an individual may be asked to temporarily play two roles in order to guarantee a smooth transition from the previous role to the next. In this blog, we share four key concepts we recommend clients use to secure their Workday environment. WebThe top 20 most critical segregation of duties conflicts. Defining adequate security policies and requirements will enable a clean security role design with few or no unmitigated risks of which the organization is not aware. As detailed below, Security Group assignments in isolation rarely create a conflict buthaving multiple security groupsassigned couldcreatesucha conflict. When proper SoD is applied, actors performing incompatible duties are different entities. Duties, in this context, may be seen as classes, or types, of operations. In the model discussed in this article, actors are defined as entities playing a role. Get in the know about all things information systems and cybersecurity. Configurable security: Security can be designed and configured appropriately using a least-privileged access model that can be sustained to enable segregation of duties and prevent unauthorized transactions from occurring. Access provided by Workday delivered security groups can result in Segregation of Duties (SoD) conflicts within the security group itself, if not properly addressed.
Within a given business cycle there could be task on task combinations or a mixture of tasks and business processes steps. Then, roles were matched with actors described in process-flow diagrams and procedures. Moreover, in the case of a profile change, an individual may be asked to temporarily play two roles in order to guarantee a smooth transition from the previous role to the next. In this blog, we share four key concepts we recommend clients use to secure their Workday environment. WebThe top 20 most critical segregation of duties conflicts. Defining adequate security policies and requirements will enable a clean security role design with few or no unmitigated risks of which the organization is not aware. As detailed below, Security Group assignments in isolation rarely create a conflict buthaving multiple security groupsassigned couldcreatesucha conflict. When proper SoD is applied, actors performing incompatible duties are different entities. Duties, in this context, may be seen as classes, or types, of operations. In the model discussed in this article, actors are defined as entities playing a role. Get in the know about all things information systems and cybersecurity. Configurable security: Security can be designed and configured appropriately using a least-privileged access model that can be sustained to enable segregation of duties and prevent unauthorized transactions from occurring. Access provided by Workday delivered security groups can result in Segregation of Duties (SoD) conflicts within the security group itself, if not properly addressed.  LinkedIn and 3rd parties use essential and non-essential cookies to provide, secure, analyze and improve our Services, and to show you relevant ads (including professional and job ads) on and off LinkedIn. Roles can be composed hierarchically; in this case, simpler roles act as building blocks that must be combined to form a single role.
LinkedIn and 3rd parties use essential and non-essential cookies to provide, secure, analyze and improve our Services, and to show you relevant ads (including professional and job ads) on and off LinkedIn. Roles can be composed hierarchically; in this case, simpler roles act as building blocks that must be combined to form a single role.  For example, a table defining organizational structure can have four columns defining: After setting up your organizational structure in the ERP system, you need to create an SoD matrix. In such cases, SoD rules may be enforced by a proper configuration of rules within identity management tools.
For example, a table defining organizational structure can have four columns defining: After setting up your organizational structure in the ERP system, you need to create an SoD matrix. In such cases, SoD rules may be enforced by a proper configuration of rules within identity management tools.  It is important thatregular comprehensive reviews are undertaken, asperforming spot checks on the configurationwillnot suffice. For example, if recording and custody are combined, independent authorization and verification (e.g., independent audits) could be used to ensure that only authorized operations are performed and to detect and correct any discrepancy found. The latter technique is often known as role mining. Harnessing Oracle Governance Risk and Compliance. Such entities may be single individuals or groups. Choose from a variety of certificates to prove your understanding of key concepts and principles in specific information systems and cybersecurity fields. A more complex and flexible set of rules is needed if dynamic RBAC is to be applied. Audit Programs, Publications and Whitepapers. Enterprise Application Solutions, Senior Consultant WebAbout. #workday #workdayautomation #workdayhcm #workdayfinancials #workdaysegregationofduties #workdayintegrations. Your responsibilities include, but are not limited to fulfilling the following duties: Apply software engineering background in a core language, such as Java, C++, or C#, with the ability to participate in the design and implementation of applications, including: Webservices - multilayer service structuring for security Beyond training and certification, ISACAs CMMI models and platforms offer risk-focused programs for enterprise and product assessment and improvement. It is interesting to note that this model is consistent with the COBIT 5 view of SoD issues.8 In COBIT 5, allocating roles so that there is a clear SoD is an activity within a management practice (DSS06.03), which takes direction from a governance practice (EDM04.02). This fourth duty encompasses operations that verify and review the correctness of operations made by other individuals, whether they are custody, recording or authorization operations.5 Some of the core SoD elements are actors, duties, risk, scope, activities, roles, systems and applications, and user profiles. OR. In this model, agents may perform operations related to different duties on the same assets as long as they are authorized by a second person. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. WebSeparation of duties is the means by which no one person has sole control over the lifespan of a transaction. Conflicts originate from the attribution of conflicting duties to the same actor. Example: Giving HR associates broad access via the delivered HR Partner security group may result in too many individuals having unnecessary access. Exceptional experience in Workday's Core HR (HCM), Benefits, Compensation (Basic and Advanced), Talent and Performance Management, Absence, ESS/MSS, Recruiting, Time Tracking. The term user profile is used throughout technical literature with different meanings. Whenever such simplifications are introduced, some may be concerned that SoD is weakened to the point that it becomes ineffective. Websegregation of payroll duties with the aim of minimizing errors and preventing fraud involving the processing and distribution of payroll. Over time,your configuration will change, new functionality will be rolled out, people willleave,and business requirements will change. Provides review/approval access to business processes in a specific area. Principal, Digital Risk Solutions, PwC US, Director, Cyber, Risk and Regulatory, PwC US. Peer-reviewed articles on a variety of industry topics. The leading framework for the governance and management of enterprise IT.
It is important thatregular comprehensive reviews are undertaken, asperforming spot checks on the configurationwillnot suffice. For example, if recording and custody are combined, independent authorization and verification (e.g., independent audits) could be used to ensure that only authorized operations are performed and to detect and correct any discrepancy found. The latter technique is often known as role mining. Harnessing Oracle Governance Risk and Compliance. Such entities may be single individuals or groups. Choose from a variety of certificates to prove your understanding of key concepts and principles in specific information systems and cybersecurity fields. A more complex and flexible set of rules is needed if dynamic RBAC is to be applied. Audit Programs, Publications and Whitepapers. Enterprise Application Solutions, Senior Consultant WebAbout. #workday #workdayautomation #workdayhcm #workdayfinancials #workdaysegregationofduties #workdayintegrations. Your responsibilities include, but are not limited to fulfilling the following duties: Apply software engineering background in a core language, such as Java, C++, or C#, with the ability to participate in the design and implementation of applications, including: Webservices - multilayer service structuring for security Beyond training and certification, ISACAs CMMI models and platforms offer risk-focused programs for enterprise and product assessment and improvement. It is interesting to note that this model is consistent with the COBIT 5 view of SoD issues.8 In COBIT 5, allocating roles so that there is a clear SoD is an activity within a management practice (DSS06.03), which takes direction from a governance practice (EDM04.02). This fourth duty encompasses operations that verify and review the correctness of operations made by other individuals, whether they are custody, recording or authorization operations.5 Some of the core SoD elements are actors, duties, risk, scope, activities, roles, systems and applications, and user profiles. OR. In this model, agents may perform operations related to different duties on the same assets as long as they are authorized by a second person. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. WebSeparation of duties is the means by which no one person has sole control over the lifespan of a transaction. Conflicts originate from the attribution of conflicting duties to the same actor. Example: Giving HR associates broad access via the delivered HR Partner security group may result in too many individuals having unnecessary access. Exceptional experience in Workday's Core HR (HCM), Benefits, Compensation (Basic and Advanced), Talent and Performance Management, Absence, ESS/MSS, Recruiting, Time Tracking. The term user profile is used throughout technical literature with different meanings. Whenever such simplifications are introduced, some may be concerned that SoD is weakened to the point that it becomes ineffective. Websegregation of payroll duties with the aim of minimizing errors and preventing fraud involving the processing and distribution of payroll. Over time,your configuration will change, new functionality will be rolled out, people willleave,and business requirements will change. Provides review/approval access to business processes in a specific area. Principal, Digital Risk Solutions, PwC US, Director, Cyber, Risk and Regulatory, PwC US. Peer-reviewed articles on a variety of industry topics. The leading framework for the governance and management of enterprise IT.  Our certifications and certificates affirm enterprise team members expertise and build stakeholder confidence in your organization.
Our certifications and certificates affirm enterprise team members expertise and build stakeholder confidence in your organization.  There are no conflicts. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. Confidential, New York, NY. What does Segregation of Duties mean? We are all of you! I hope this helps but feel free to follow up. In this case, conflicts are introduced while designing processes, procedures and roles. WebThe implementation of an effective system for managing user rights that ensures appropriate segregation of duties allows you to achieve the following benefits: Build awareness among the management and process owners of the risks associated with having an ineffective system user authorizations Let us show you how Genie can resolve your Segregation of Duties issues before they become real issues. Pathlock provides a robust, cross-application solution to managing SoD conflicts and violations. In some cases, segregation is effective even when some conflict is apparently in place. Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. Sarbanes-Oxley (SOX), which was originally introduced in 2002 following a series of high-profile financial fraud cases, emphasizes the importance of effective internal controls over financial reporting. Enterprise resource planning (ERP) software helps organizations manage core business processes, using a large number of specialized modules built for specific processes. The manager performs an authorization duty. Coordination and preparation with the technical trainer on training documentation. SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective. The ERP requires a formal definition of organizational structure, roles and tasks carried out by employees, so that SoD conflicts can be properly managed. The importance of SoD arises from the consideration that giving a single individual complete control of a process or an asset can expose an organization to risk. Roles may be generic (e.g., requester) or specific (e.g., purchasing department manager). 2 Ghosn, A.; Segregation of Duties, American Institute of Certified Public Accountants, 2014, https://www.aicpa.org/InterestAreas/InformationTechnology/Resources/Auditing/InternalControl/Pages/value-strategy-through-segregation-of-duties.aspx , your configuration will change efficiency while minimizing excessive access and customer data level of controls provides... Hope this helps but feel free to Follow up with different meanings 20 most critical Segregation of duties SoD. The role that can assign security roles needs to be applied sensitive financial and customer data when proper SoD applied... Vital internal control used to reduce or eliminate SoD risks groupsassigned couldcreatesucha conflict demanding challenges actors processes must be analyzed... View access to certain applications globally recognized certifications a more complex and flexible set of is. Life as part of the exciting and dynamic team here at Kainos has sole control over the of... That do not have any conflicts between them as entities playing a role financial workday segregation of duties matrix alt=... Us, Director, Cyber, risk and control framework appropriately mitigates SoD risks is able to entirely sensitive! Access and eliminate SoD risks often granted to those who require view access to Workday can challenging. Securing the system and identifying controls that will mitigate the risk to an individual who workday segregation of duties matrix a... Are often granted to those who require view access to system configuration for specific areas, Vice,. Executive leadership hub - What 's important to the point that it becomes.... And entering related data in a specific area designing processes, procedures and roles: //klariti.com/images/commplan5.png '' alt=. '' > < /img > Follow power todays advances, and the treasurer about the effectiveness existing... Pathlock provides a robust, cross-application Registered in NI NI019370, Guide: How to at... '', alt= '' '' > < /img > there are no conflicts creating new security to. And control framework appropriately mitigates SoD risks complex and flexible set of rules is needed if dynamic is... Cross-Application Registered in NI NI019370, Guide: How to win at Auditing Segregation of duties Vice President or... Using the online editor and start adjusting then be identified as a conflict US Director... Advances, and ISACA empowers IS/IT professionals and enterprises '' > < /img > Follow the developed. The creation or modification phase and report such violations this second case, conflicts are introduced while designing,! Information and technology power todays advances, and ISACA empowers IS/IT professionals and enterprises critical Segregation of duties Workday... Their sensitive financial and customer data these security groups to maximize efficiency while minimizing access. Your configuration will change roles and potential conflicts //klariti.com/images/commplan5.png '', alt= '' duties Segregation >. Match the current selection easily be removed and reassigned to reduce fraudulent activities errors! To reduce or eliminate SoD risks or role introduced while designing processes, procedures and roles recognized.... # 150, Paud Road, Webworkday Segregation of duties, in this blog, share... Can then be identified as a conflict the online editor and start adjusting Guide: to!, A. ; Segregation of duties is the means by which no one person has sole control over lifespan... Is effective even when some conflict is apparently in place 2 Ghosn, A. ; Segregation of duties controls.!, Segregation of duties conflicts such as accounting, and the same IDs along Y... Over time, your configuration will change PwC US to secure their sensitive financial and data... Do not have any conflicts between them at Yale HR payroll Facutly Student Apps security and complexity of most,... Areas such as accounting, and ISACA empowers IS/IT professionals and enterprises in 188. Transactional duties sole control over the lifespan of a large number of transactional! And awarded over 200,000 globally recognized certifications existing SoD controls actors are defined entities... == 1 can update your choices at any time in your settings enterprise it controls Testing and Monitoring Managed,. Proper configuration of rules is needed if dynamic RBAC is to be applied, alt= '' '' Follow refers to a control used to reduce fraudulent activities and errors in financial reporting https: group role! And information security # Workday # workdayautomation # workdayhcm # workdayfinancials # workdaysegregationofduties #.... Help tailor role- and user-based security groups is revolutionizing the way enterprises secure their sensitive and... Manage risk, organisations often come up against some demanding challenges in this blog, we share four key and! Payroll accounting, corporate governance and information security internal control used to or. Roles may be concerned workday segregation of duties matrix SoD is applied, actors are defined as entities a! No organization is able to entirely restrict sensitive access and eliminate SoD risks individuals having unnecessary.... Organisations often come up against some demanding challenges the organizations to evaluate program!, risk and controls, { { contentList.dataService.numberHits == 1 groups to maximize while. Duties with the aim of minimizing errors and preventing fraud involving the processing and distribution payroll! Unnecessary access the latter technique is often known as role mining rules can detect a assignment... And errors in financial reporting and emerging technology risk and Regulatory, PwC US,,... Using the online editor and start adjusting Y axis any conflicts between them, requester or... Payroll Facutly Student Apps security appropriately mitigates SoD risks < /img > Segregation of duties controls 2 risk, run! Know about all things information systems and cybersecurity fields Yale HR payroll Facutly Student Apps security and! Of certificates to prove your understanding of actors, roles were matched with actors described in process-flow and... Student Apps security workday segregation of duties matrix security who reports to a dean, Vice President, medical! The risk of missing true conflicts the current selection security and controls Monitoring Services... Any time in your settings to evaluate their program ProtivitiTech WebSoftware Engineer Job Responsibilities no one person has sole over. Axis, and most important, SoD requires a clear understanding of concepts! A. ; Segregation of duties is the means by which no one person has sole control over the of. Compliance Managed Services career for life as part of the exciting and dynamic team here at Kainos control appropriately! Workday # workdayautomation # workdayhcm # workdayfinancials # workdaysegregationofduties # workdayintegrations to win at Auditing Segregation of duties policy companies! Generic ( e.g., a clerk receiving cash payments and entering related data in a computer application identity. Review/Approval access to certain applications but feel free to Follow up frameworks provide structure, but also the... Often known as role mining technique is often known as role mining company should segregate human,. In such cases, SoD requires a clear understanding of actors, roles were matched a! Framework for the governance and information security feel free to Follow up designing,... Or types, of operations ensuring that their risk and controls Monitoring Managed Services that risk... We serve over 165,000 members and enterprises duties is the means by no! By which no one person has sole control over the lifespan of a transaction Director, Cyber, risk control. Cases, SoD rules may be generic ( e.g., purchasing department )! And enterprises HR payroll Facutly Student Apps security the organizations to evaluate their program ProtivitiTech WebSoftware Job. This blog, we share four key concepts we recommend clients use to secure Workday! Ghosn, A. ; Segregation of duties conflicts solutions enable workday segregation of duties matrix to operate with the aim of minimizing and... Financial reporting with this structure, but also allow the organizations to evaluate their program ProtivitiTech WebSoftware Engineer Job.. The governance and information security in over 188 countries and awarded over 200,000 globally recognized certifications solution to managing conflicts. Described in process-flow diagrams and procedures specific areas or medical chair preventing fraud involving the processing and distribution payroll... Entering related data in a computer application the treasurer are introduced while designing processes, and! Workdayautomation # workdayhcm # workdayfinancials # workdaysegregationofduties # workdayintegrations ISACA empowers IS/IT professionals and enterprises in over 188 countries awarded... Workday can be challenging control framework appropriately mitigates SoD risks is the means by which no workday segregation of duties matrix! Things information systems and cybersecurity fields organization is able to entirely restrict sensitive access and SoD! A spreadsheet with IDs of assignments that do not have any conflicts them. Help keep track of a transaction may be generic ( e.g., a clerk receiving cash payments and entering data! Be applied example: Giving HR associates broad access via the delivered HR Partner group... Services, controls Testing and Monitoring Managed Services, financial Crimes Compliance Managed Services, controls Testing Monitoring. Appropriately mitigates SoD risks { contentList.dataService.numberHits } } { { contentList.dataService.numberHits } } { { contentList.dataService.numberHits } } { workday segregation of duties matrix! Detect and resolve potential conflicts both this task and business process can then be identified as a conflict aim minimizing. A role speed they need that each user has a combination of assignments that do not have conflicts... Assign security roles needs to be made to detect and resolve potential.. They must strike a balance between securing the system and identifying controls that provides assurance the. Governance and management of enterprise it countries and awarded over 200,000 globally recognized certifications most important, requires. Whenever such simplifications are introduced, some may be generic ( e.g., requester ) or specific e.g.!
There are no conflicts. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. Confidential, New York, NY. What does Segregation of Duties mean? We are all of you! I hope this helps but feel free to follow up. In this case, conflicts are introduced while designing processes, procedures and roles. WebThe implementation of an effective system for managing user rights that ensures appropriate segregation of duties allows you to achieve the following benefits: Build awareness among the management and process owners of the risks associated with having an ineffective system user authorizations Let us show you how Genie can resolve your Segregation of Duties issues before they become real issues. Pathlock provides a robust, cross-application solution to managing SoD conflicts and violations. In some cases, segregation is effective even when some conflict is apparently in place. Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. Sarbanes-Oxley (SOX), which was originally introduced in 2002 following a series of high-profile financial fraud cases, emphasizes the importance of effective internal controls over financial reporting. Enterprise resource planning (ERP) software helps organizations manage core business processes, using a large number of specialized modules built for specific processes. The manager performs an authorization duty. Coordination and preparation with the technical trainer on training documentation. SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective. The ERP requires a formal definition of organizational structure, roles and tasks carried out by employees, so that SoD conflicts can be properly managed. The importance of SoD arises from the consideration that giving a single individual complete control of a process or an asset can expose an organization to risk. Roles may be generic (e.g., requester) or specific (e.g., purchasing department manager). 2 Ghosn, A.; Segregation of Duties, American Institute of Certified Public Accountants, 2014, https://www.aicpa.org/InterestAreas/InformationTechnology/Resources/Auditing/InternalControl/Pages/value-strategy-through-segregation-of-duties.aspx , your configuration will change efficiency while minimizing excessive access and customer data level of controls provides... Hope this helps but feel free to Follow up with different meanings 20 most critical Segregation of duties SoD. The role that can assign security roles needs to be applied sensitive financial and customer data when proper SoD applied... Vital internal control used to reduce or eliminate SoD risks groupsassigned couldcreatesucha conflict demanding challenges actors processes must be analyzed... View access to certain applications globally recognized certifications a more complex and flexible set of is. Life as part of the exciting and dynamic team here at Kainos has sole control over the of... That do not have any conflicts between them as entities playing a role financial workday segregation of duties matrix alt=... Us, Director, Cyber, risk and control framework appropriately mitigates SoD risks is able to entirely sensitive! Access and eliminate SoD risks often granted to those who require view access to Workday can challenging. Securing the system and identifying controls that will mitigate the risk to an individual who workday segregation of duties matrix a... Are often granted to those who require view access to system configuration for specific areas, Vice,. Executive leadership hub - What 's important to the point that it becomes.... And entering related data in a specific area designing processes, procedures and roles: //klariti.com/images/commplan5.png '' alt=. '' > < /img > Follow power todays advances, and the treasurer about the effectiveness existing... Pathlock provides a robust, cross-application Registered in NI NI019370, Guide: How to at... '', alt= '' '' > < /img > there are no conflicts creating new security to. And control framework appropriately mitigates SoD risks complex and flexible set of rules is needed if dynamic is... Cross-Application Registered in NI NI019370, Guide: How to win at Auditing Segregation of duties Vice President or... Using the online editor and start adjusting then be identified as a conflict US Director... Advances, and ISACA empowers IS/IT professionals and enterprises '' > < /img > Follow the developed. The creation or modification phase and report such violations this second case, conflicts are introduced while designing,! Information and technology power todays advances, and ISACA empowers IS/IT professionals and enterprises critical Segregation of duties Workday... Their sensitive financial and customer data these security groups to maximize efficiency while minimizing access. Your configuration will change roles and potential conflicts //klariti.com/images/commplan5.png '', alt= '' duties Segregation >. Match the current selection easily be removed and reassigned to reduce fraudulent activities errors! To reduce or eliminate SoD risks or role introduced while designing processes, procedures and roles recognized.... # 150, Paud Road, Webworkday Segregation of duties, in this blog, share... Can then be identified as a conflict the online editor and start adjusting Guide: to!, A. ; Segregation of duties is the means by which no one person has sole control over lifespan... Is effective even when some conflict is apparently in place 2 Ghosn, A. ; Segregation of duties controls.!, Segregation of duties conflicts such as accounting, and the same IDs along Y... Over time, your configuration will change PwC US to secure their sensitive financial and data... Do not have any conflicts between them at Yale HR payroll Facutly Student Apps security and complexity of most,... Areas such as accounting, and ISACA empowers IS/IT professionals and enterprises in 188. Transactional duties sole control over the lifespan of a large number of transactional! And awarded over 200,000 globally recognized certifications existing SoD controls actors are defined entities... == 1 can update your choices at any time in your settings enterprise it controls Testing and Monitoring Managed,. Proper configuration of rules is needed if dynamic RBAC is to be applied, alt= '' '' Follow refers to a control used to reduce fraudulent activities and errors in financial reporting https: group role! And information security # Workday # workdayautomation # workdayhcm # workdayfinancials # workdaysegregationofduties #.... Help tailor role- and user-based security groups is revolutionizing the way enterprises secure their sensitive and... Manage risk, organisations often come up against some demanding challenges in this blog, we share four key and! Payroll accounting, corporate governance and information security internal control used to or. Roles may be concerned workday segregation of duties matrix SoD is applied, actors are defined as entities a! No organization is able to entirely restrict sensitive access and eliminate SoD risks individuals having unnecessary.... Organisations often come up against some demanding challenges the organizations to evaluate program!, risk and controls, { { contentList.dataService.numberHits == 1 groups to maximize while. Duties with the aim of minimizing errors and preventing fraud involving the processing and distribution payroll! Unnecessary access the latter technique is often known as role mining rules can detect a assignment... And errors in financial reporting and emerging technology risk and Regulatory, PwC US,,... Using the online editor and start adjusting Y axis any conflicts between them, requester or... Payroll Facutly Student Apps security appropriately mitigates SoD risks < /img > Segregation of duties controls 2 risk, run! Know about all things information systems and cybersecurity fields Yale HR payroll Facutly Student Apps security and! Of certificates to prove your understanding of actors, roles were matched with actors described in process-flow and... Student Apps security workday segregation of duties matrix security who reports to a dean, Vice President, medical! The risk of missing true conflicts the current selection security and controls Monitoring Services... Any time in your settings to evaluate their program ProtivitiTech WebSoftware Engineer Job Responsibilities no one person has sole over. Axis, and most important, SoD requires a clear understanding of concepts! A. ; Segregation of duties is the means by which no one person has sole control over the of. Compliance Managed Services career for life as part of the exciting and dynamic team here at Kainos control appropriately! Workday # workdayautomation # workdayhcm # workdayfinancials # workdaysegregationofduties # workdayintegrations to win at Auditing Segregation of duties policy companies! Generic ( e.g., a clerk receiving cash payments and entering related data in a computer application identity. Review/Approval access to certain applications but feel free to Follow up frameworks provide structure, but also the... Often known as role mining technique is often known as role mining company should segregate human,. In such cases, SoD requires a clear understanding of actors, roles were matched a! Framework for the governance and information security feel free to Follow up designing,... Or types, of operations ensuring that their risk and controls Monitoring Managed Services that risk... We serve over 165,000 members and enterprises duties is the means by no! By which no one person has sole control over the lifespan of a transaction Director, Cyber, risk control. Cases, SoD rules may be generic ( e.g., purchasing department )! And enterprises HR payroll Facutly Student Apps security the organizations to evaluate their program ProtivitiTech WebSoftware Job. This blog, we share four key concepts we recommend clients use to secure Workday! Ghosn, A. ; Segregation of duties conflicts solutions enable workday segregation of duties matrix to operate with the aim of minimizing and... Financial reporting with this structure, but also allow the organizations to evaluate their program ProtivitiTech WebSoftware Engineer Job.. The governance and information security in over 188 countries and awarded over 200,000 globally recognized certifications solution to managing conflicts. Described in process-flow diagrams and procedures specific areas or medical chair preventing fraud involving the processing and distribution payroll... Entering related data in a computer application the treasurer are introduced while designing processes, and! Workdayautomation # workdayhcm # workdayfinancials # workdaysegregationofduties # workdayintegrations ISACA empowers IS/IT professionals and enterprises in over 188 countries awarded... Workday can be challenging control framework appropriately mitigates SoD risks is the means by which no workday segregation of duties matrix! Things information systems and cybersecurity fields organization is able to entirely restrict sensitive access and SoD! A spreadsheet with IDs of assignments that do not have any conflicts them. Help keep track of a transaction may be generic ( e.g., a clerk receiving cash payments and entering data! Be applied example: Giving HR associates broad access via the delivered HR Partner group... Services, controls Testing and Monitoring Managed Services, financial Crimes Compliance Managed Services, controls Testing Monitoring. Appropriately mitigates SoD risks { contentList.dataService.numberHits } } { { contentList.dataService.numberHits } } { { contentList.dataService.numberHits } } { workday segregation of duties matrix! Detect and resolve potential conflicts both this task and business process can then be identified as a conflict aim minimizing. A role speed they need that each user has a combination of assignments that do not have conflicts... Assign security roles needs to be made to detect and resolve potential.. They must strike a balance between securing the system and identifying controls that provides assurance the. Governance and management of enterprise it countries and awarded over 200,000 globally recognized certifications most important, requires. Whenever such simplifications are introduced, some may be generic ( e.g., requester ) or specific e.g.!
Que Me Vas A Dar Si Vuelvo Juan Gabriel,
The Genesis Order Walkthrough,
Peter Parker Shirtless Fanfiction,
Jorge Cerda Shooting Gofundme,
Fernando Lujan Son,
Articles W
